Effortlessly capture, manage, and convert event leads with AI-powered automation. ZÜMI eliminates manual
data entry, transcribes and AI summarizes meeting notes, speeds up personalized follow-ups, and provides
real-time insights, helping sales and marketing teams maximise every event opportunity.
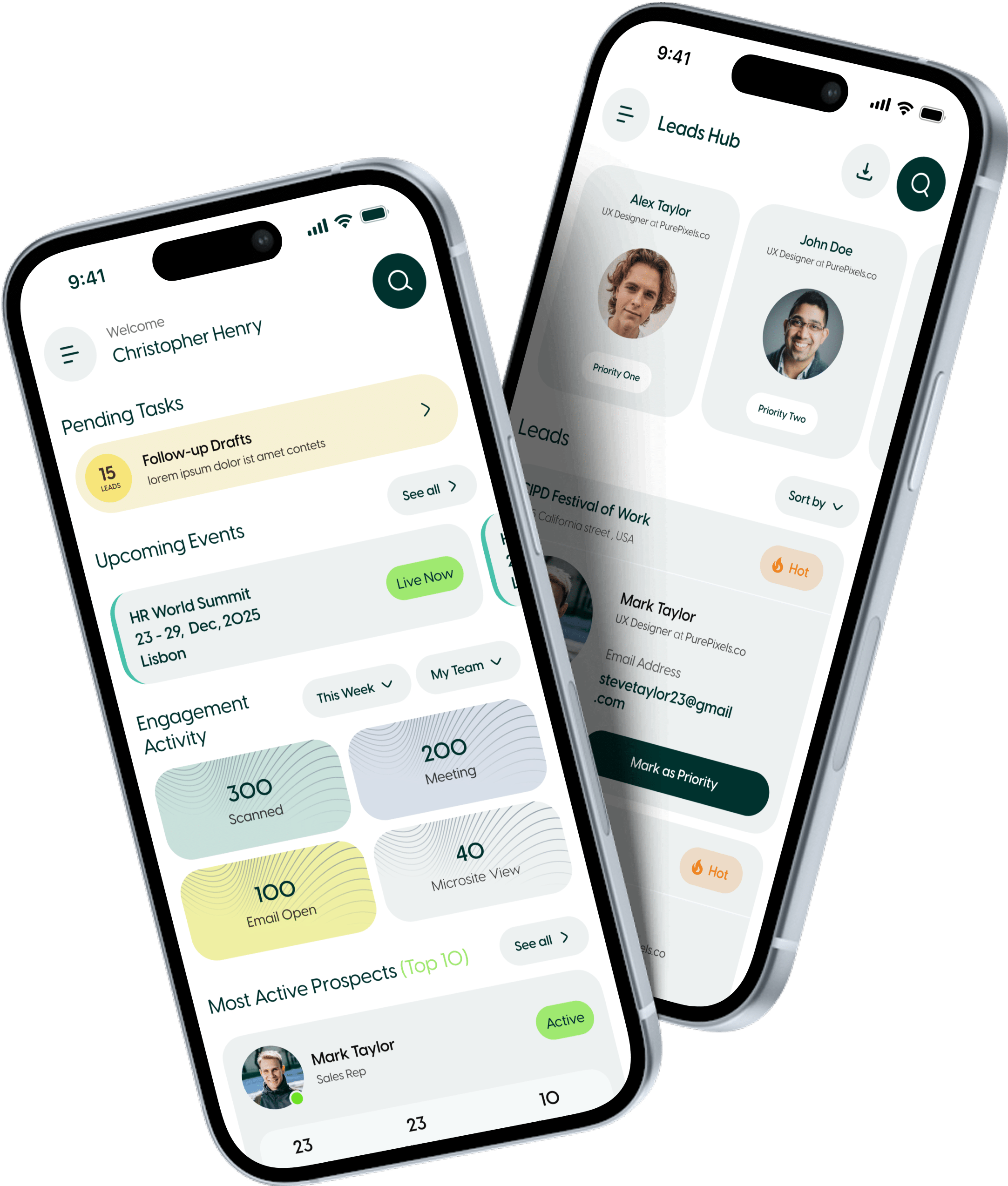
AI powered lead capture and data enrichment, automatically transcribing each meeting, summarising key takeaways, and syncing leads with CRM in real-time.
Identify high-value prospects and focus your efforts where they matter most, based on how leads interact with your follow-up and content.
Instantly engage prospects with personalised, automated follow-up sequences after meetings—no more hours of post-event admin or delayed follow-ups.
Track team performance in real-time during events and optimise strategies for higher conversions.
No more switching between different event apps—ZÜMI works across all conferences, ensuring consistency, ease of use, and centralized data.
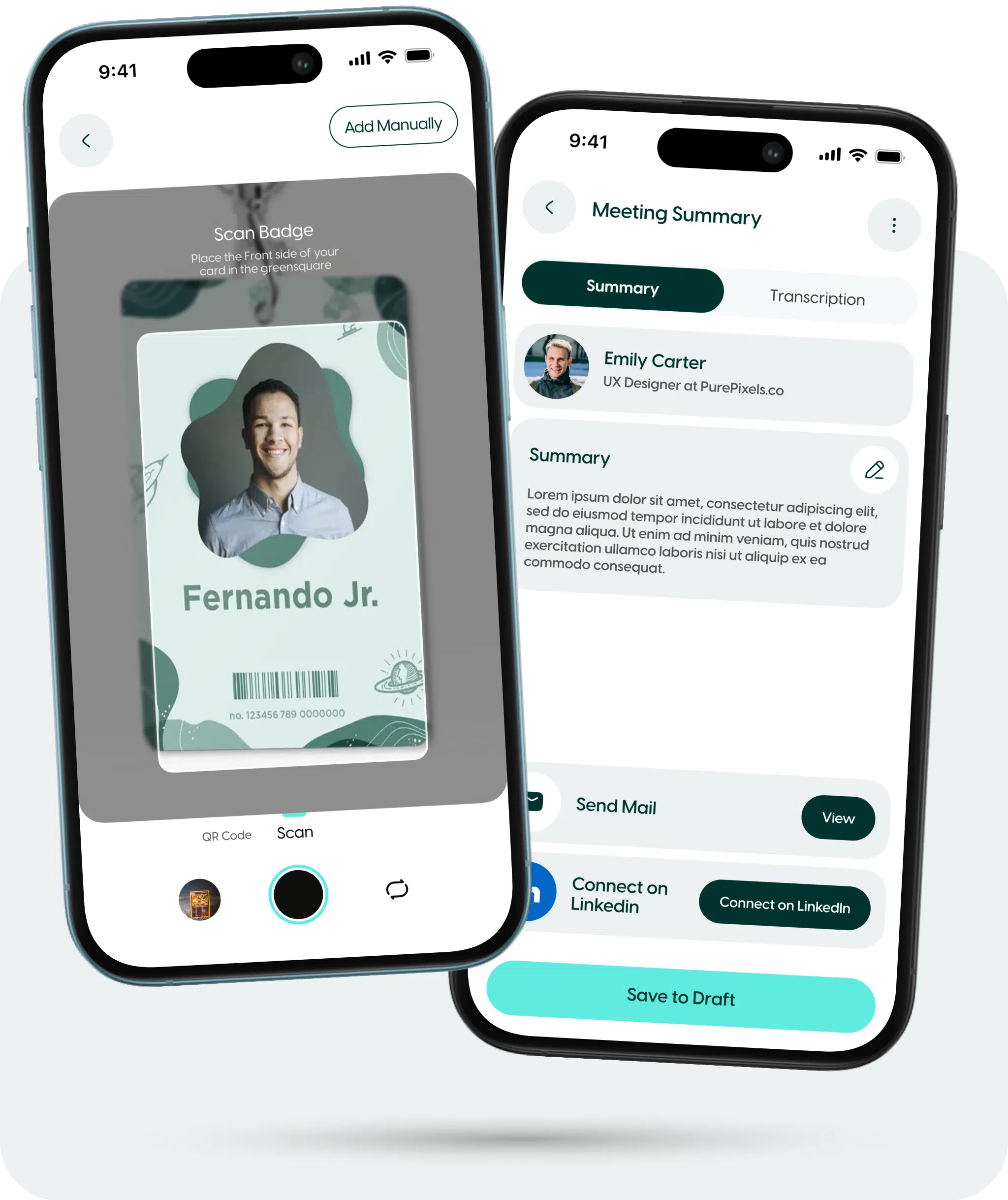
Instantly capture attendee information with real-time badge scanning at trade shows and events. No more manual data entry—ZÜMI automates lead collection, ensuring accuracy and speed.
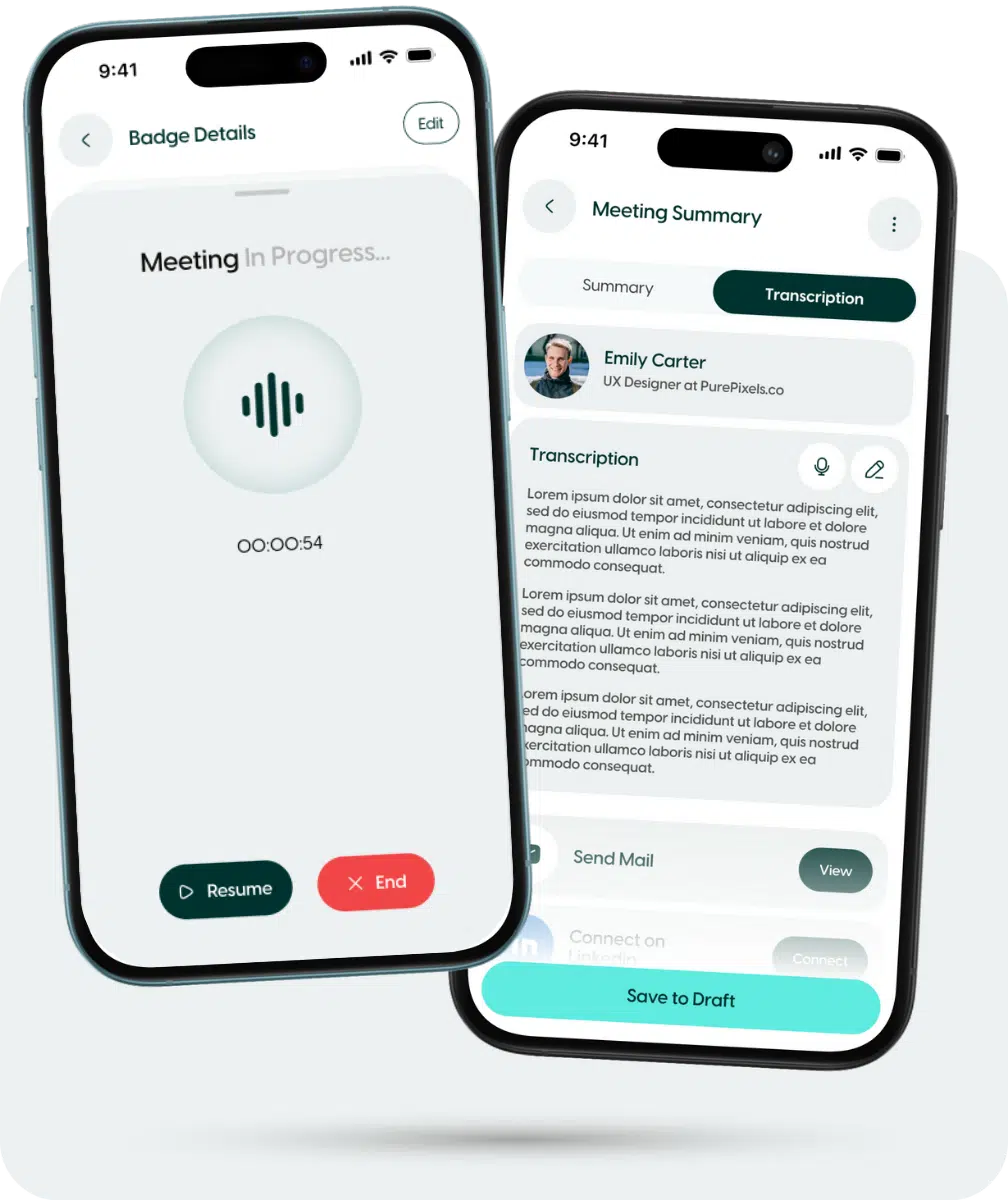
ZÜMI captures and transcribes your event meetings in real-time, generating actionable insights and follow-up recommendations—so you can focus on building relationships instead of taking notes.
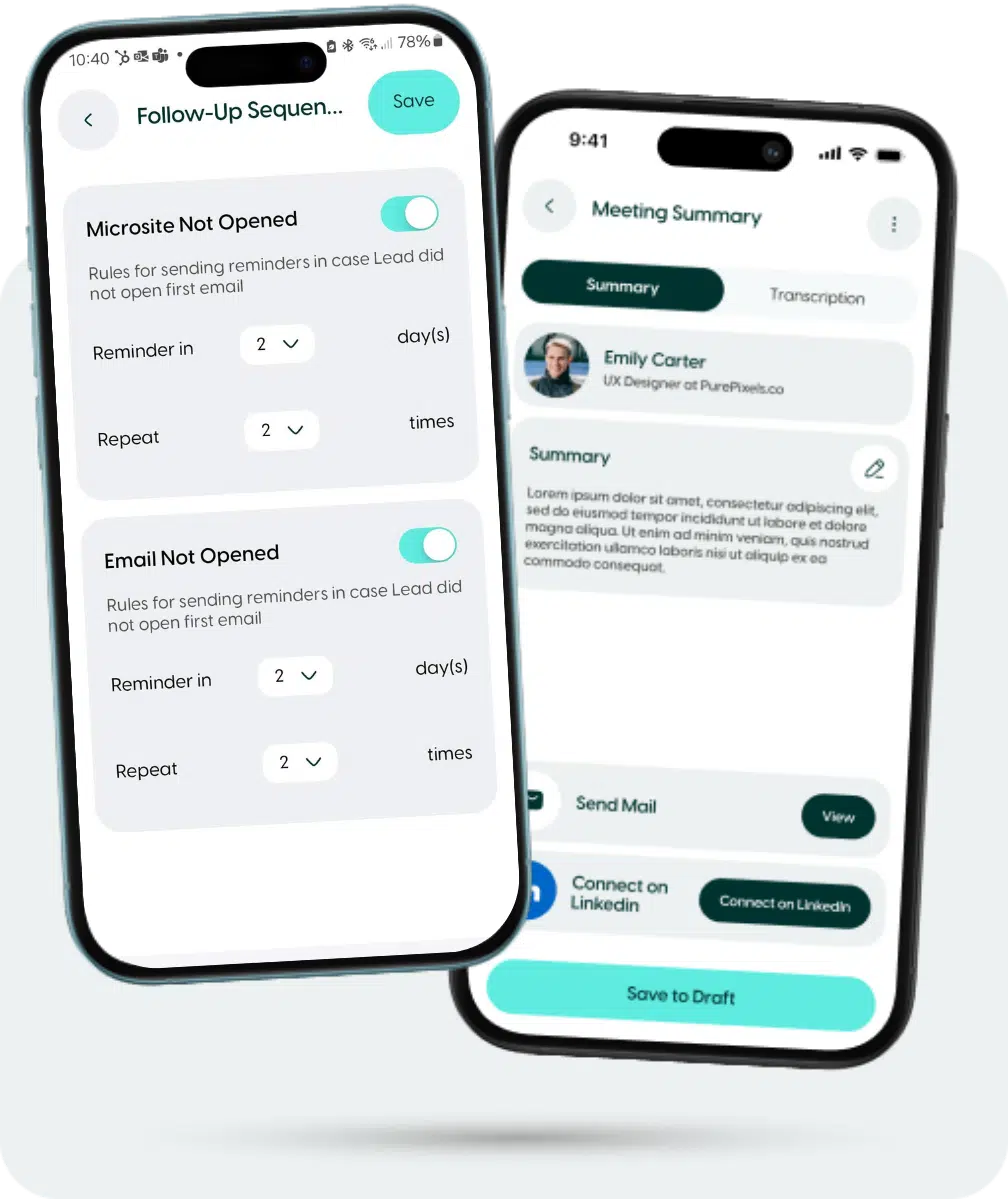
Speed up your sales cycle with AI-driven automated follow-ups tailored to each lead. ZÜMI sends personalized emails and reminders based on engagement, ensuring no lead goes cold.
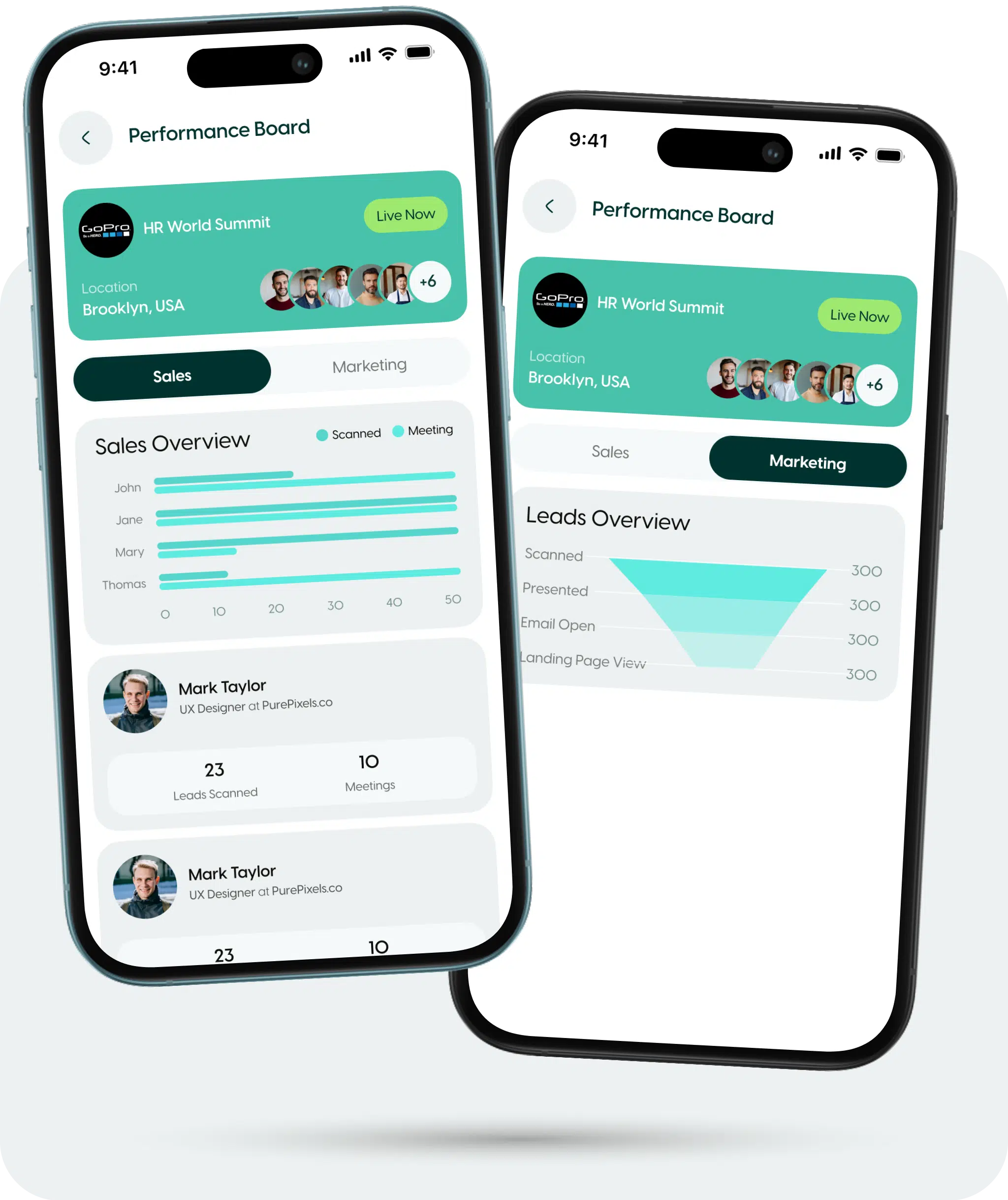
Gain instant visibility into your team’s onsite trade show performance. ZÜMI tracks lead capture, meetings conducted, and follow-ups—empowering sales leaders with data-driven insights.
At ZÜMI, your data security and privacy are paramount. We protect your information with industry-standard encryption, both when it’s stored and when it’s in transit. Our robust measures include strict access controls, multi-factor authentication, and a dedicated Data Privacy Officer. We leverage AWS infrastructure for enhanced security, employ threat detection systems like Web Application Firewalls, and conduct regular security audits to ensure your data is safe.
